DevOps, DevSecOps and CI/CD are synonymous with one word - automation. Automating their workflows gives developers the ability to deliver consistency, time savings, and useful insights into their software development life cycle (SDLC). But automation is only as efficient as your weakest link or most cumbersome bottleneck, which can sometimes be security testing.
Security testing has traditionally been carried out either manually or quite late in the process. Sometimes security testing relied on legacy tools that are slow, are not developer friendly and do not effectively integrate into the continuous integration (CI) pipeline.
To maintain rapid release cycles, you are either forced to wait until the manual security checks and validations are complete (which could take weeks), or accept the risk and deploy (which is unfortunately more common). Either of these choices can result in significant vulnerabilities in production, with issues only being remediated months after a release is completed (if at all), and resulting in an insurmountable technical and security debt.
This bottleneck counteracts the benefits gained from automation. To compound matters, bottlenecked security testing becomes such a pain point that it is routinely ignored, or even removed from the workflow entirely. This article will describe some ways to keep security testing automation an active part of your pipeline so you can continue to deliver timely and secure apps of consistently high quality.
Prerequisites
To follow the examples in this article, you will need to have a few things in place.
- GitHub account
- A CircleCI account
- Cloud account (for this example we will use an AWS account)
- A NexPloit.app account (it is free) to run the security tests
Automated security testing as part of your CircleCI workflow
To maintain security testing automation as part of your workflow requires that your tooling has attributes that complement and keep up with the fast pace:
- Seamlessly integrated into your CI
- Designed for developers. Tooling built for cyber security professionals, with complicated test setup and configurations, will not work for developers
- Intuitive scan optimizations and the ability to leverage config files as code
- The ability to test every build and commit, quickly, while also identifying vulnerabilities
- Automated removal of false positives in a way that does not delay (and annoy) developers (and the security team)
- Clear and effective remediation guidelines
With this kind of tooling in place, automated testing surfaces real issues that can be remediated early and often, and developers will start trusting the outcome. Integrating and running these tests to start getting security compliance on every build, is very simple, as I will show in the next few sections of this article.
Integrating and Configuring CircleCI and NexPloit
NeuraLegion has a CircleCI orb. For this example, though, we will use a vulnerable application in a GitHub repository and set up a CircleCI workflow.
We will run an initial security scan using NexPloit against the target, where CircleCI will break the build as per our configuration and the results can be viewed for remediation. The code repository for this example contains a publicly available repository of an example CircleCI YAML configuration file. This runs a scan against an intentionally vulnerable benchmark application called Broken Crystals. Feel free to use this target as a test project.
This YAML file contains the configuration for the security scanning, the pipeline itself (called nexploit), with details of the repo and execution steps.
Install the NexPloit CLI utility so you can use the Nexploit API to run, poll status, and stop scans.
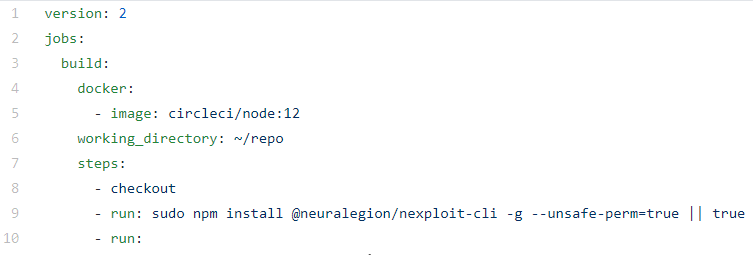
Next we need to provide details for the scan set up:
- A crawler will be used on the target to automatically detect the attack surface
- NEXPLOIT_TOKEN – a token required to use the Nexploit API
- The length of the scan and polling intervals and timeout
- Breakpoint, which in this instance is the build failing on detection of a medium severity issue
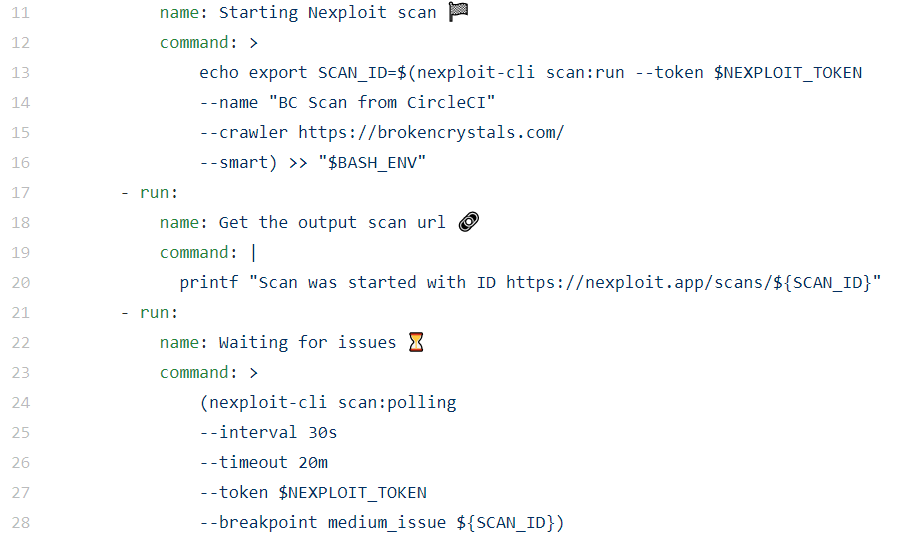
So, let’s look at how you set up an automatic scan in CircleCI.
First, we need to add our integrations. If you haven’t already, add your GitHub and Nexploit.app integrations.
Integrating GitHub with CircleCI
Probably the most simple process, there are no plugins to install and integration really is out-of-the-box. Simply sign in with your GitHub account and CircleCI mirrors your GitHub team permissions and privileges, so you can start building right away. CircleCI automatically runs your build and test processes whenever you commit code in GitHub.
Integrating NeuraLegion’s Nexploit.app with CircleCI
In CircleCI, navigate to your Projects and select the repo you would like to integrate with automated testing.
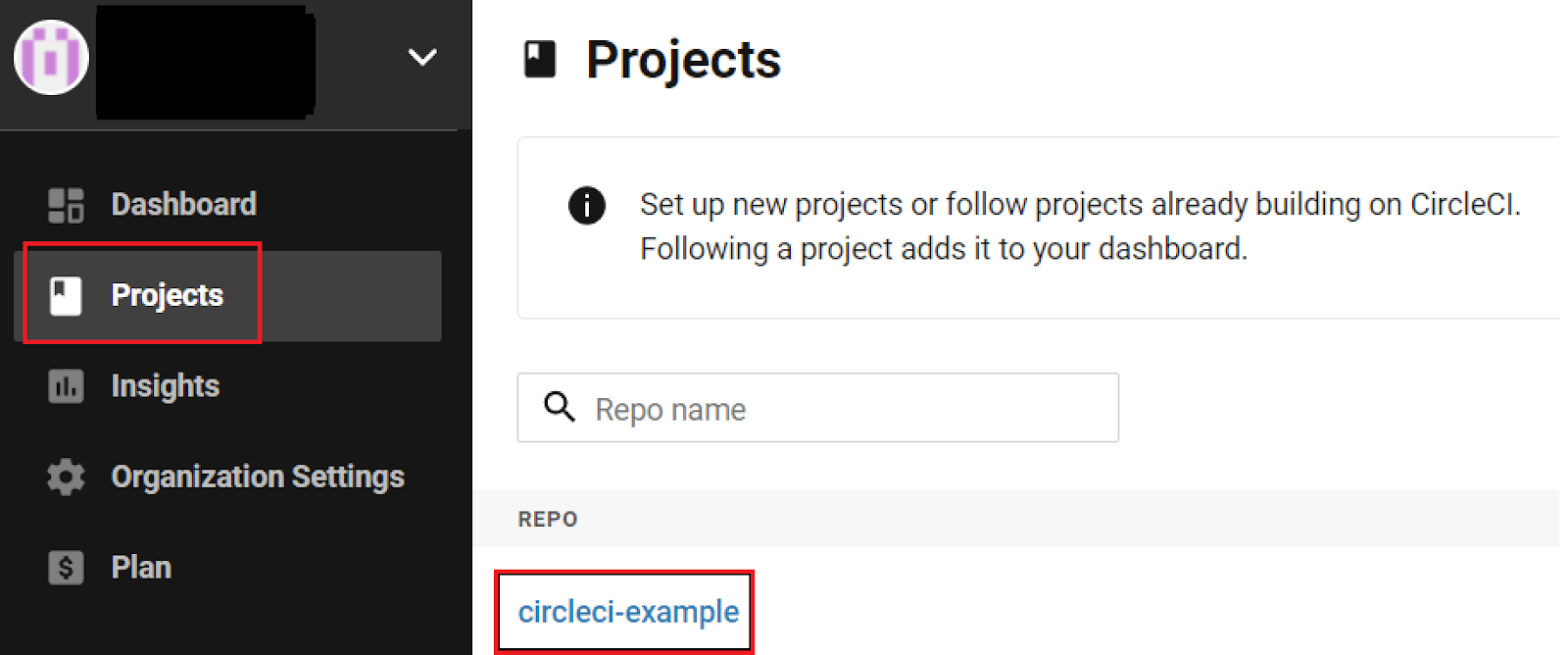
Get Nexploit.app API Key
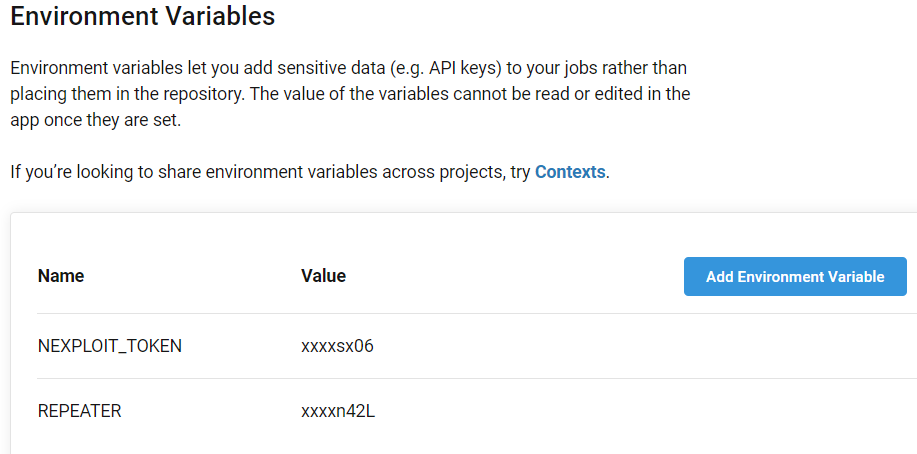
- Go to Project Settings, then Environment Variables to add the API keys and token for the Nexploit repeater/CLI.
- In the nexploit.app, go to User Settings, click Create New API Key.
- Add a ‘Name’ for the API key
- Under ‘Choose Scopes’, select all.
- Create and copy the token. This can be used in the CircleCI Platform to set up the integration.
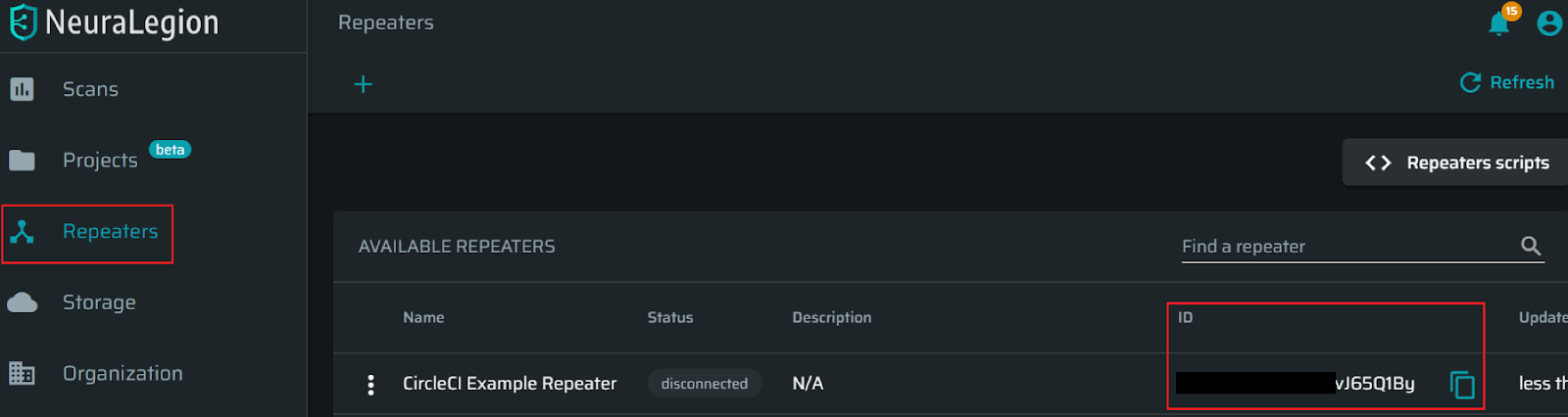
Get the Repeater ID
- Go to Repeaters then press + to set up a new repeater.
- Add a ‘Name’
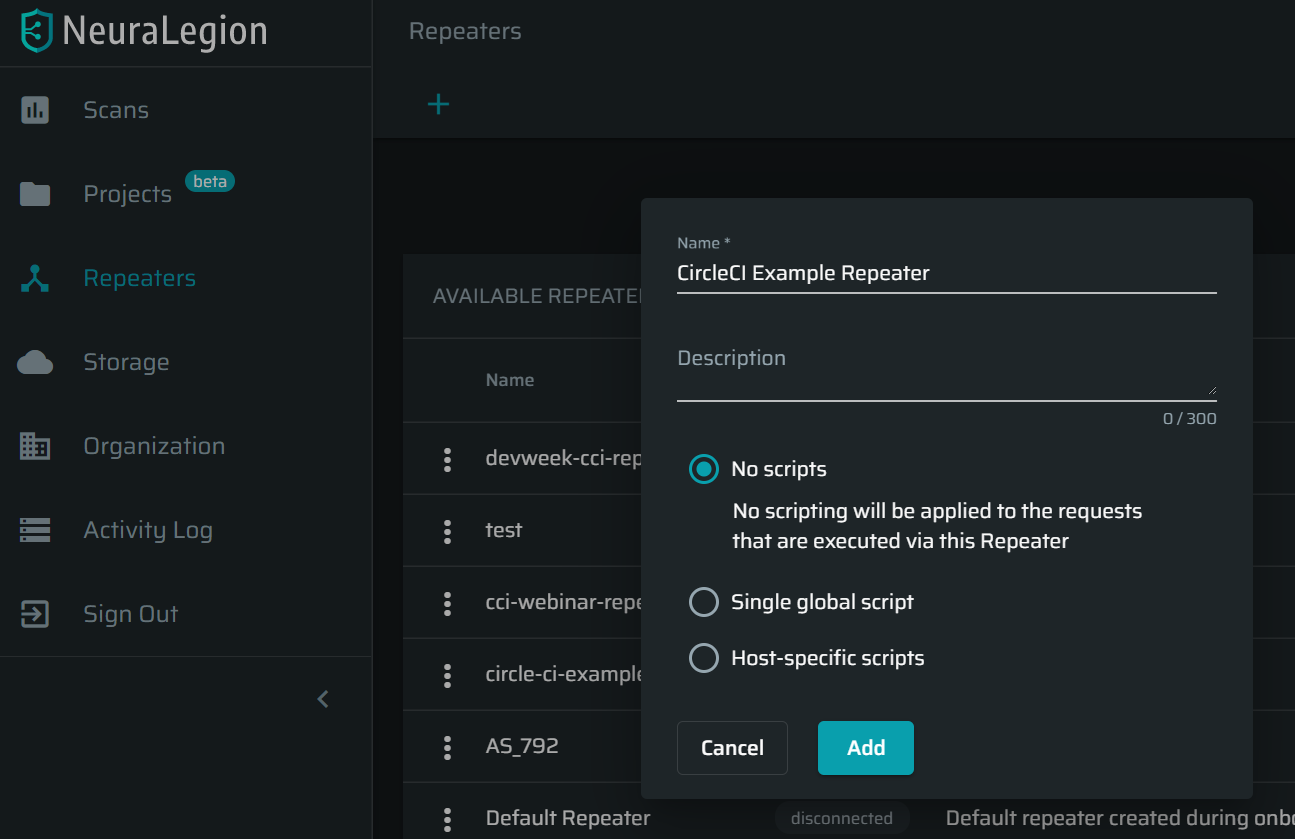
- Under the list of repeaters, copy the new Repeater ID you have generated.
The new API Key and Repeater ID can now be used to set up your CircleCI environment variables: NEXPLOIT_TOKEN, and REPEATER.
Your next commit will initiate a workflow and build with CircleCI. NexPloit will run a security test against that commit.
 : .zoomable }
: .zoomable }
As specified in the config.yaml, the environment is spun up, the environment variables are prepared, a new NexPloit security scan is started against the target, and we are polling for results.
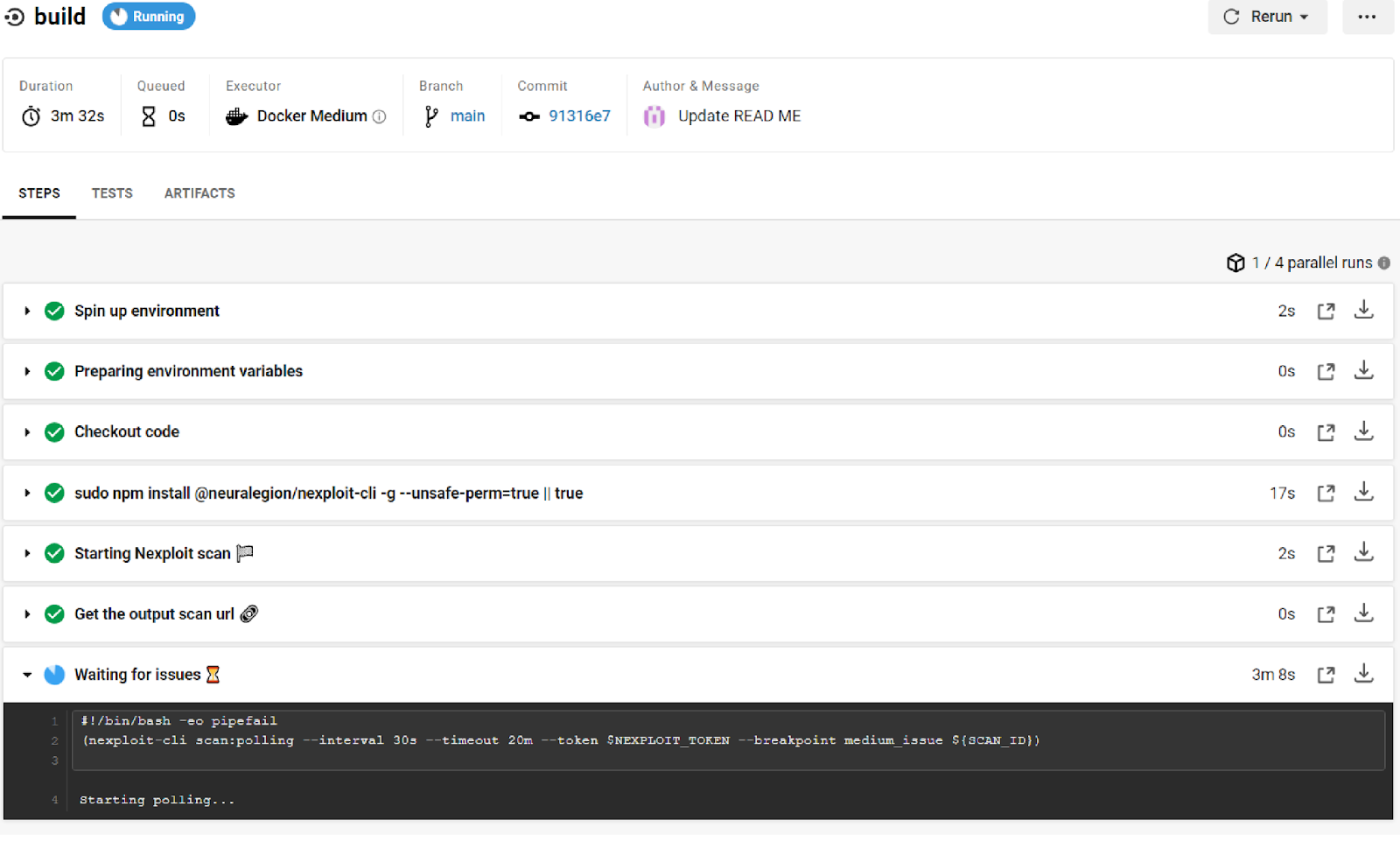
After a short time, NexPloit will find a medium-level issue. As we specified in the configuration file when this breakpoint is met, the build fails and the scan is set to stop. Removing this ‘Stop Scan’ step in the configuration will fail the build, but continue to run the scan against the target so that any additional vulnerabilities can be detected.
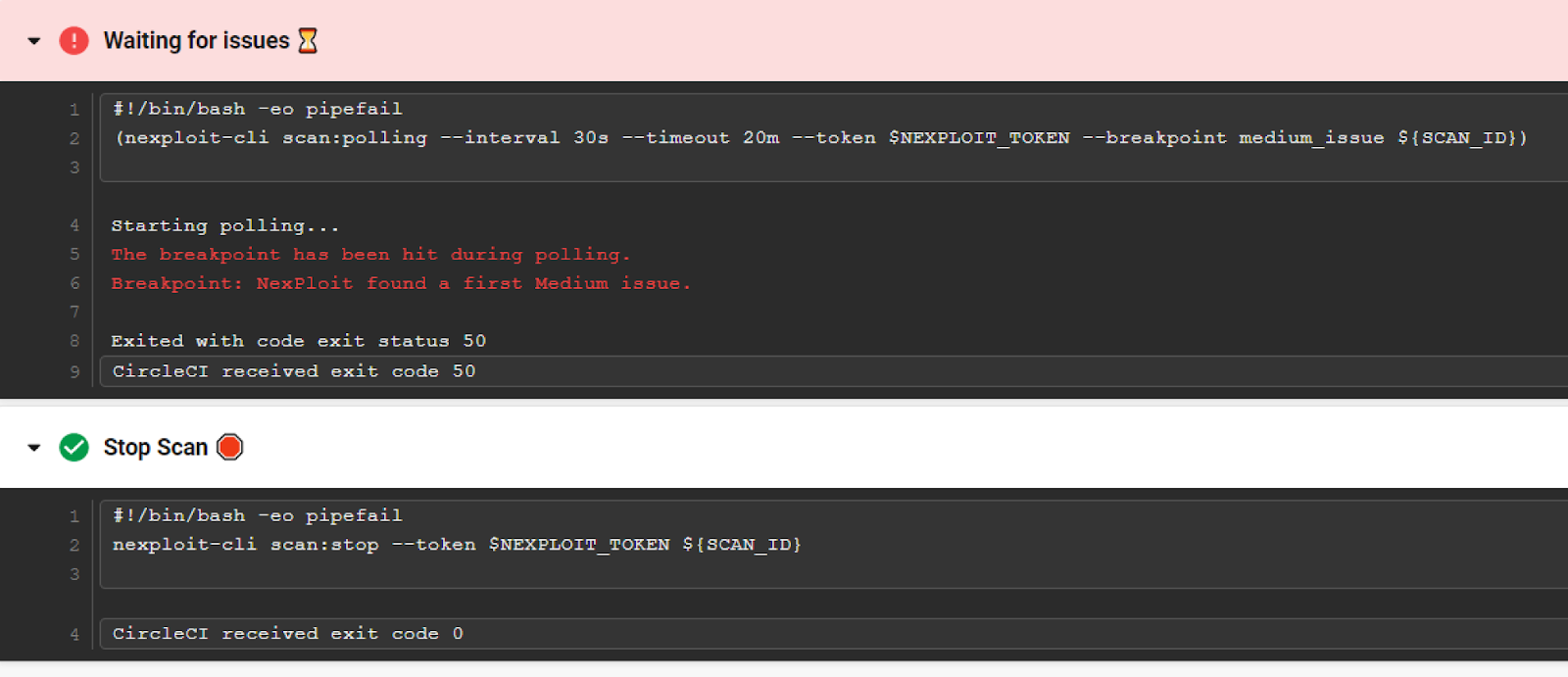
We can now look at the security scan status and results using the NexPloit dashboard to check the status.
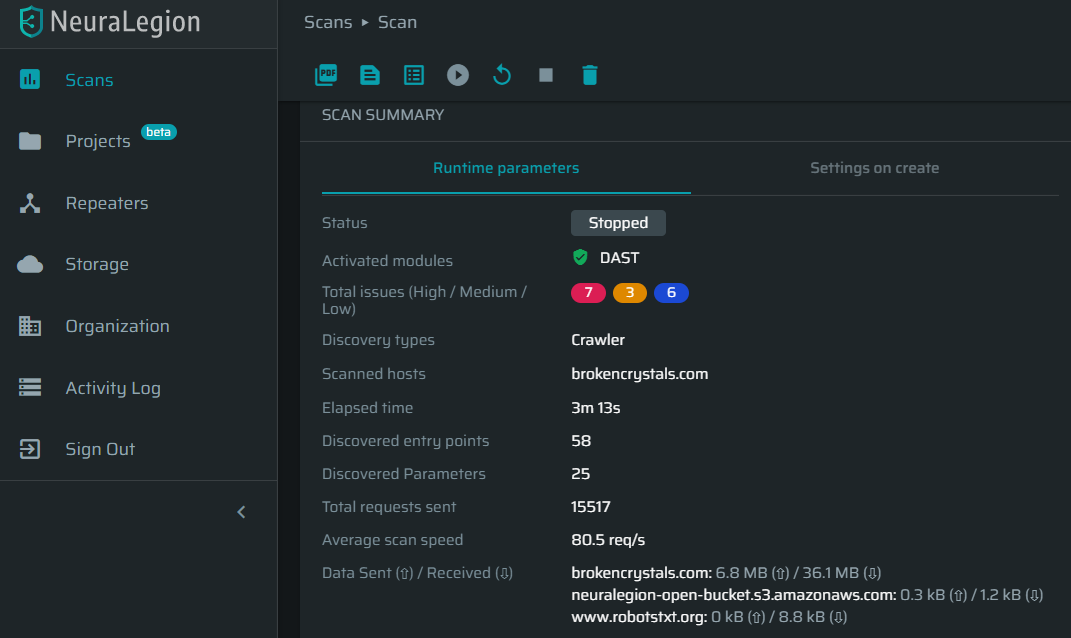
The scanner has already detected a number of automatically validated security issues on the target, ready to be fixed, without the need for any manual validation.
The results provide the developer with information they need to understand the issue, how to replicate it, and how to fix it, with remediation guidelines.
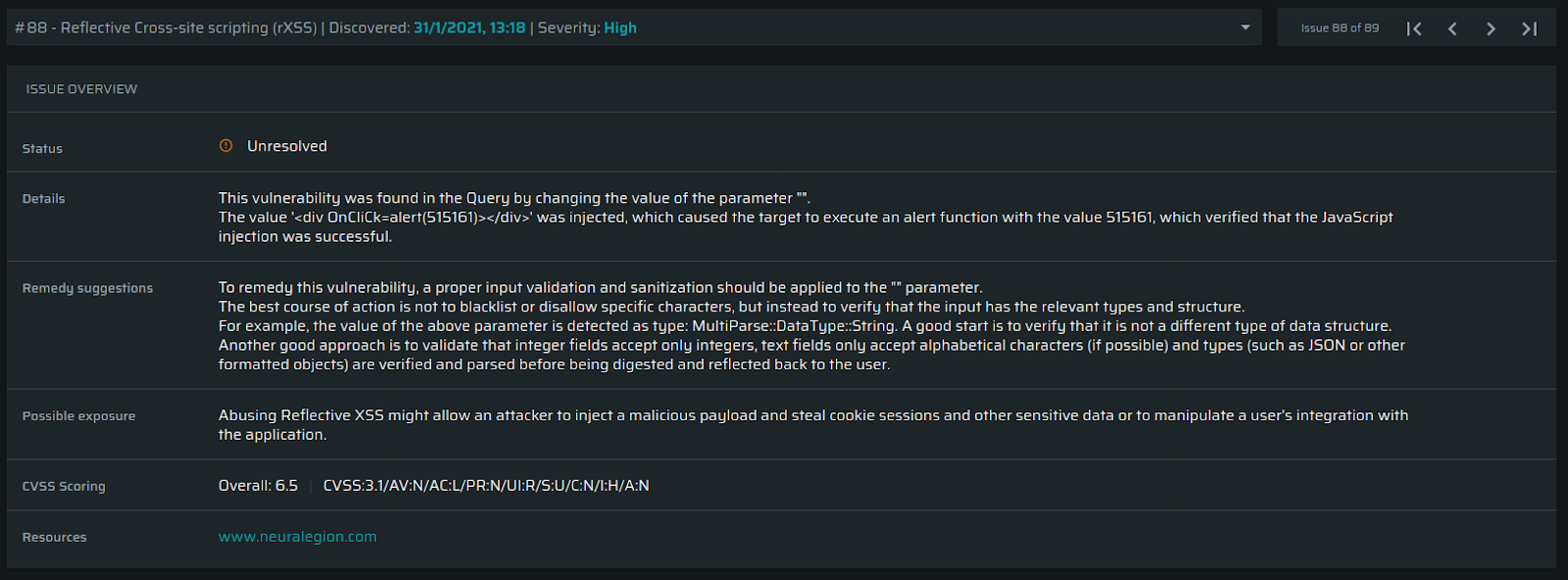
The request, with a diff-like view (what was added/deleted) is provided, as well as the response, headers, and the body.
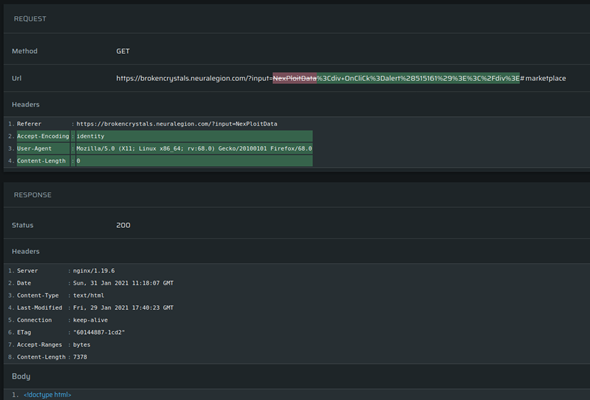
In this Cross-Site Scripting (XSS) example, there is additional evidence in the form of a screenshot as a proof of concept, so you know the vulnerability is there.
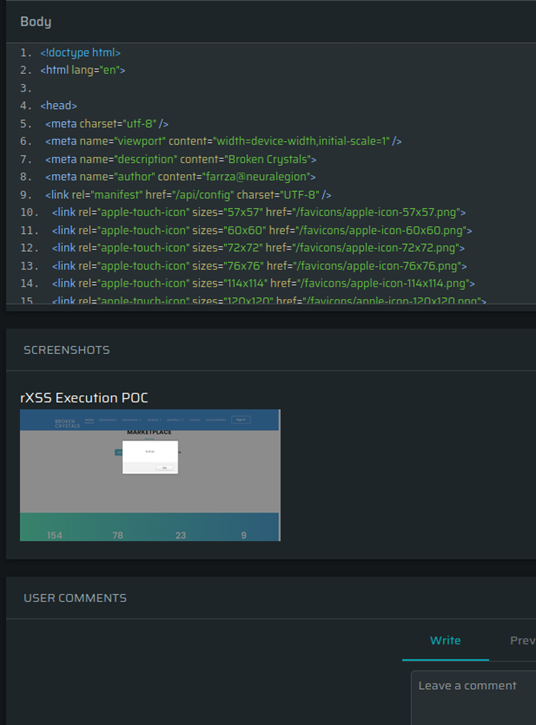
Nexploit integrates with JIRA so a ticket can be automatically raised with each issue detected, or you can connect JIRA and CircleCI with a plugin.
Conclusion
Connecting NeuraLegion’s DAST AppSec scanning into your CircleCI pipeline is simple, straightforward and an automated step in your workflow. You can also continue to use your other integrations, such as ticketing systems like JIRA. NexPloit can scan your web apps or APIs (SOAP, REST, GraphQL), with the results of any vulnerabilities organized and explained in a developer-friendly way that describes vulnerabilities and how to remediate and fix them.
With CircleCI and NeuraLegion, you can create end-to-end deployment pipelines in minutes that includes security testing as an integral part, without builds failing due to false alerts. The result is secure products being deployed with a streamlined CI process in place. Read about how Fastlane leveraged CircleCI and NeuraLegion to automate developing and rolling out new features, quickly.
Oliver Moradov is a VP at NeuraLegion, and an expert in Application Security Testing (DAST) automation for DevOps and DevSecOps. NeuraLegion delivers a developer focused DAST platform. Discover how you can use CircleCI and NexPloit together to automate AppSec testing in your pipelines to be secure by design. You can get started right away, by signing up for your CircleCI free trial today.






